If we told you that we've found the Achilles Heel of all malware attacks and have developed a patented technique to disarm all malware including ransomware, before it can detonate, would it be worth a few minutes of your time to determine if we can back-up these claims?
There is a lot of noise in the marketplace regarding ransomware and how to mitigate the effects of an attack. Several solutions, mostly in the data protection space, can legitimately help you to minimize the damage IF you get hit by a successful ransomware attack. You should absolutely deploy the data protection solution that best fits your corporate environment. But that's not what we're talking about in terms of disarming all malware before it can detonate.
A lot of focus is on keeping malware out of your environment with firewalls, zero-trust network access architectures, malware detection tools like EDR and anti-virus solutions and so on. Again, important tools to deploy within your corporate IT environment, but not what we're talking about in terms of stopping ransomware in its tracks.
Use this link to schedule an introductory conversation with one of our cybersecurity specialists.
Malware can generally be categorized as one of five different types.
Watch this 4:39 video on how AppGuard works.
Interestingly, ransomware isn't recognized as a "type" of malware. What defines ransomware is the outcome it seeks, or so-called "Actions on the Objective". Typically, ransomware encrypts data files once it has achieved "Command and Control" of the environment, with a demand for payment in order to unencrypt the data.
At it's core, malware is intended to give criminals unauthorized access to your network in order for them to do something that you won't like, such as encrypting your data (ransomware), or stealing your customer data or intellectual property, or something else.
Malware uses vulnerabilities in poorly designed applications and utilities to do things like obtain escalated network or application privileges as an administrator, develop a persistent "backdoor" for easy re-entry, or disabling any protections so they can remain undetected.
The malware attack lifecycle can be described in these steps.
Within the malware attack lifecycle steps above, you need to stop the malware before it can perform installation. It's only after installation that your detection tools like anti-virus or EDR systems kick into action, but by then it could be too late.
Once the malware achieves installation status, you'll need to deploy your incident response plan and hope that you've got a very well thought out playbook.
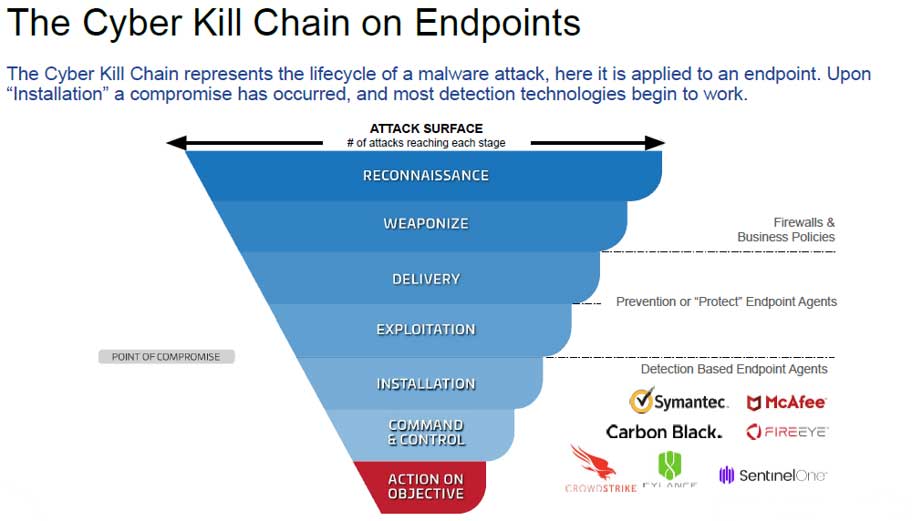
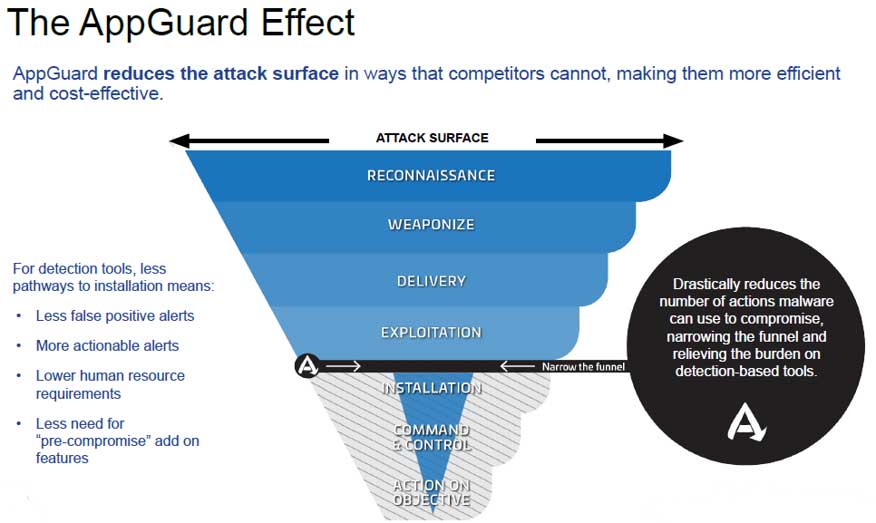
AppGuard stops malware between the exploitation step and the installation step. Even though malware may have gotten through some of your lines of defense, it cannot detonate until it's been able to perform some kind of installation or system alteration.
Once malware has gotten to the Exploitation step, it hijacks an application or script and uses the hijacked process to help it gain access to core areas of your operating system. These core elements reside in "System Space" and include things like program files, Windows registry, and other high privilege low-risk directories that a typical end-user without administrator privileges cannot write to. Windows is designed to launch applications and utilities from System Space.
These hijacked applications or scripts are exploited within "User Space" which is an area associated with the user profile and includes things like user directories and desktops, download folders, removable media such as USB drives, network drives, and other high risk, low privilege directories.
Some applications execute from User Space, but that's a sign of a poorly written application or more often it's an attempted malware execution.
In order to achieve the Installation step, the malware needs the hijacked process to fool the environment in order to gain access into the System Space. By treating anything that launches outside of the System Space as dangerous and blocking it (a zero trust application access solution), we've disarmed the malware. This is how we stop all malware and ransomware in its tracks.
AppGuard has been in use by over 6,000 companies around the world for over 10 years, and it has never been successfully compromised.
Use this link to schedule an introductory conversation with one of our cybersecurity specialists.